Apps help to get a financial overview. But do you also know that you can use it to file your tax return, take out insurance and make investments? […]
Finances are and remain one of the biggest stressors in our everyday lives. Whether in partnerships or in the job-financial stress affects us in many aspects of life. How good that there is a suitable solution for every problem.
Over the past decade, numerous young startups have developed mobile apps that help us manage our finances. Thanks to new regulatory regulations (e.g. PSD2), banks are losing the monopoly on our customer data. Young fintechs use modern data analysis and AI solutions to realize optimization potential. Bureaucratic processes are digitized and suddenly done quite comfortably on the way to work. In this article, I will show you the possibilities of taking your own finances to the next level via an app.
Digital household books and financial managers
In the first step of financial planning, it is important to provide an overview of the current situation. Household books have been used for decades to track monthly expenses and discover savings potential. Instead of relying on paper and pen, today there is a wide selection of apps with exciting features. Expenses are automatically categorized, statistics and charts visualize your consumer behavior and budgets can be better adhered to via alarm function. Especially popular budget apps are the Money Manager, My Budget Book and Monefy.
 Money Manager is one of the top rated personal finance apps (c) Money Manager
Money Manager is one of the top rated personal finance apps (c) Money Manager
In addition to the household book apps, financial managers have also established themselves. These apps rely on multi-banking. This means nothing more than that you can link external bank accounts and deposits with the app. The advantage? At a glance you can see the current financial situation, even without manual updating. These apps also provide further assistance. Based on the sales data, contracts and subscriptions are automatically recognized and stored in digital contract folders. The apps are often linked to databases of large comparison portals via an interface and show potential savings in existing contracts. In the future, you will no longer have to cancel by paper – but by clicking within the app.
Get tax returns on the go
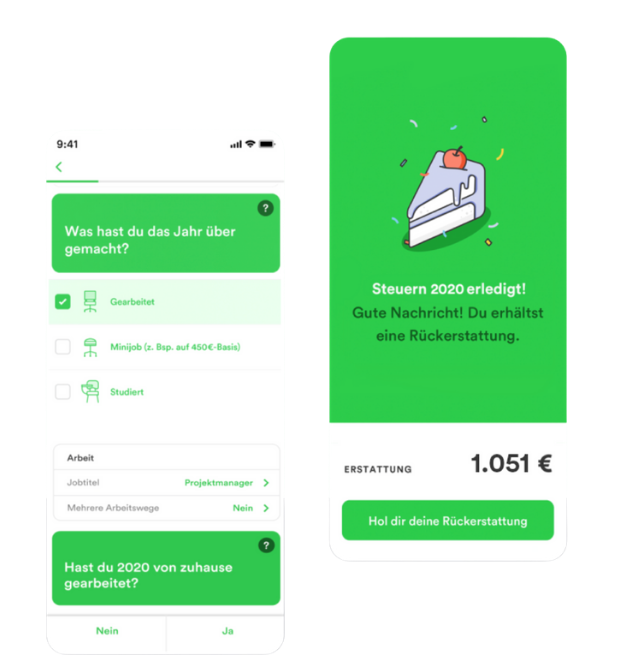
The first tax return-for most laymen this is the purest torment. Too many forms, complicated jargon and lack of overview. How good that there are tax apps. These digital helpers combine the complicated tax world with gamification. The focus is on simplicity and quick success. The German tax app Taxfix is a pioneer in Europe.
In the to-do list format, it navigates the user through his tax return. Data from documents and documents can be read via photo scan – without manual effort. In individual cases, users must nevertheless make corrections. The time savings remain great. The disruption is not in the technology, but rather in the user experience. Control apps make a complex topic a breeze. To date, most providers have not yet been able to map more complex tax cases (e.g. property owners, entrepreneurs, foreign income, etc.) – but this does not apply to the majority of taxpayers.
Manage insurance wisely
Also, insurance is one of those topics that is troublesome in the classic style. Especially the bureaucratic effort had a great influence on the emergence of so – called InsurTechs or insurance apps. Clark is one of those players who revolutionized the European insurance market. No more paper, welcome digital insurance management.
As part of the onboarding process, the personal situation and insurance coverage are asked. Subsequently, the user is shown suitable insurance policies on the basis of an algorithm, which he does not yet have. Important: Not every insurance offered actually makes sense. Before concluding a contract, one should be aware of this. A digital insurance folder that regularly searches for better policies (from a large database) completes the offer. Users don’t have to worry about anything. Insurance can be taken out, changed or terminated with one click. Eliminating paper chaos is one of the biggest benefits, especially for people who travel a lot.
Take care of retirement savings from your pocket
A lot has also happened with the investment. Gone are the days when you had to buy securities by phone or online banking. Today, you can do all these things from the comfort of your own home. One of the winners of recent years is by far the online broker Trade Republic.
The big difference from classic brokers lies in the cost advantages. Due to a lack of branch structure, neo brokers can pass on large parts of their cost advantages to their users. Another advantage is the modern user interfaces. While many banks still rely on a relatively old-fashioned design, trading apps convince with clean design and innovative features.
In addition to trading apps, banking apps such as Revolut are also increasingly relying on investment features. At Revolut you can invest in stocks, cryptocurrencies, gold and commodities. In the future, we can expect this integration of banking and investment to become standard. Switching between different apps takes time.
Conclusion
Nowadays, there is an app for everything. Whether yoga, nutrition or finance. The aim of these companies is to reduce the complexity associated with certain topics. Especially in the field of personal finance, people are still restrained-due to the high manual and bureaucratic effort. No tax potential is used, wrong insurance policies are taken out and only a few have an overview of their own finances.
Financial apps lower the barriers. It should be fun to deal with your own finances or even to file your tax return. The combination of financial planning and gamification is a disruptive development. The number of future use cases is huge – we are excited to see what the next generation of financial apps will offer.
* Carlos Link-Arad is Co-founder of Beyond Saving, as well as Founder & Managing Director of Finocate GmbH.













