Microsoft is reminding Skype for Business users to switch to the successor Microsoft Teams by the end of the month. […]

As Microsoft already announced about two years ago, is now soon finished funny with Skype for Business. The Redmonders ask in a blog entry (engl.) the remaining Skype for Business online customers to switch to Microsoft Teams by the end of the month. Microsoft provides guidance to make switching easier . The private version of Skype is still usable and received a few new features, for example, in May 2020.
By the way, since May 2021, Microsoft Teams is also available for private users (PCtipp reported). The service is almost identical to the paid business variant. This means that private users can now also write messages, make video calls, and share calendars, location, or files with friends and family.
Read also our 8 tips for using via smartphone app as well as our article “How to get the most out of Microsoft Teams”. Tips and news about teams can be found here.
More Articles

Know-how
How to protect yourself from cunning interlocutors
Manipulative interlocutors are the order of the day in meetings and negotiations. Read here, with which conversation techniques negative influences can be specifically parried. […]

News
Ransomware: what experts say about the Kaseya attack
At the beginning of July, a cyber attack hit the service provider Kaseya and spread from there to other companies. Security experts have now analyzed the unprecedented attack. […]

News
The mobile hotspot from A to Z
With a smartphone, you literally carry your own Internet access point around with you, which can also be used on the go. There is more than one way to connect. […]

Know-how
Are Ultrawide monitors recommended?
An ultrawide monitor has several advantages that improve both work and gaming, but there are also some disadvantages that you should know about. […]

Know-how
5 AI Startups That Want to Change the World
Deep learning solves challenging problems in industries as diverse as retail, manufacturing and agriculture. These companies are leading the way. […]
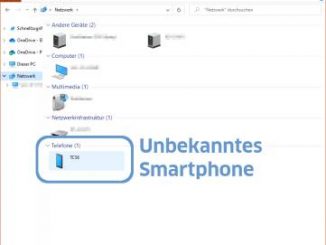
News
Windows: Unknown smartphone in your network
In your own network you do not want to have unknown devices. But if you discover one in the Windows network environment, don’t panic yet. To blame is a function called WPS, which you should turn off. […]













