Which vulnerabilities attract cybercriminals the most? And which ones do you find particularly quickly? The “2021 Cortex Xpanse Attack Surface Threat Report” from Palo Alto Networks aims to provide answers to these questions. […]

Thanks to cost-effective computing resources from the cloud, cybercriminals can more and more easily hunt for unknown security gaps. And more and more often they win the race to discover new vulnerabilities.
The IT security specialist Palo Alto Networks has now examined how quickly hackers can find and what kind of software holes they can find particularly quickly and presented the results in the “2021 Cortex Xpanse Attack Surface Threat Report”.
Specifically, Palo Alto Networks ‘ Cortex Xpanse research team has studied the publicly accessible Internet attack surface of some of the largest companies in the world. From January to March, researchers monitored scans of 50 million IP addresses connected to 50 global companies to understand how quickly attackers can identify vulnerable systems.
RDP with top position
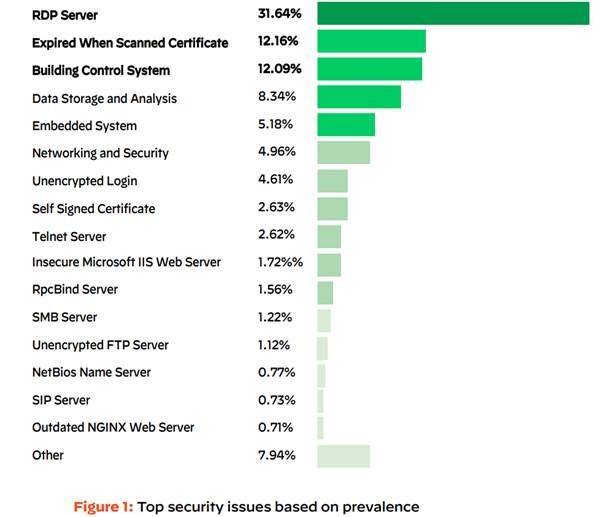 Top security incidents: Hackers find a lot of vulnerabilities here (c) Palo Alto Networks
Top security incidents: Hackers find a lot of vulnerabilities here (c) Palo Alto Networks
Among other things, it was found that almost one in three vulnerabilities discovered by the research team (32 percent) was due to problems with the widely used Remote Desktop Protocol (RDP). Its usage has skyrocketed since early 2020 as companies accelerated the move to the cloud to support remote workers. This is worrisome because RDP can provide direct admin access to servers, making it one of the most common gateways for ransomware attacks, according to Palo Alto Networks.
Other common vulnerabilities included misconfigured database servers, high-profile zero-day vulnerabilities from vendors such as Microsoft and F5, and insecure remote access via Telnet, Simple Network Management Protocol (SNMP), virtual network computing (VNC), and other protocols. Also, many of these vulnerabilities, if exploited, can allow direct administrator access.
After all: In the said cases, most of the discovered vulnerabilities could also be easily patched again, reassure the security experts somewhat.
Cloud Hub
This is also shown by the study: Cloud footprints were responsible for 79 percent of the most critical security problems that Cortex Xpanse found in global companies. This illustrates how the speed and nature of cloud computing drives the risks in modern infrastructures, the researchers point out.
Other important results of the investigation are:
- Attackers are on duty 24 hours a day: Hackers work around the clock to find vulnerable systems in corporate networks exposed to the open Internet. As a result, the threat to corporate systems has increased dramatically over the past year as companies have sought to support their remote workers. On a typical day, attackers performed a new scan once an hour, while for global companies this can take weeks.
- Attackers hurry to exploit new vulnerabilities: As soon as new vulnerabilities become known, the attackers rush to exploit them. Between January and March, scans began within 15 minutes of the release of common vulnerabilities and exposures (CVE) reports. At the zero-days that affected Microsoft Exchange Server, the attackers worked faster, launching scans within 5 minutes of Microsoft’s announcement on March 2.
- Vulnerable systems are widespread: Cortex Xpanse found that companies around the world found new serious vulnerabilities every twelve hours, that is, twice a day.












