How to work more efficiently on Mac. […]

Since Mac OS X, many applications have a much larger scope that is not accessible in everyday life. We’ll show you some useful everyday tips to make your Mac life easier.
Rename multiple files at once in Finder
1. Since OS X Yosemite, Mac users can also rename multiple files at once. To do this, select the desired objects and bring up the context menu with Ctrl+Click.
2. Then select Rename Objects.
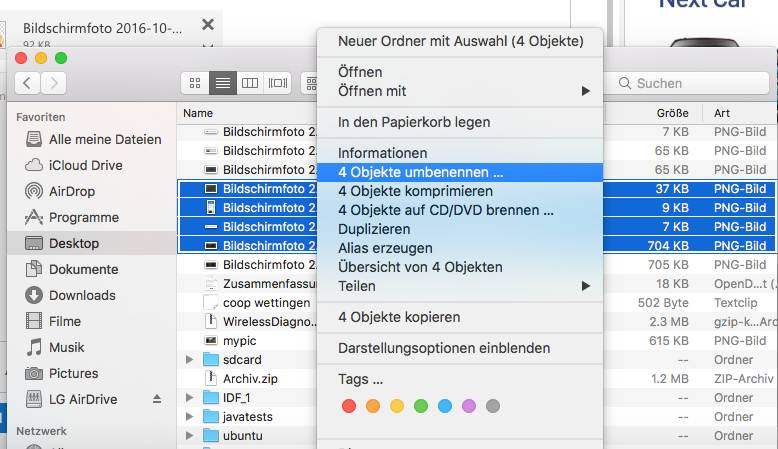 (c) PCtipp.ch
(c) PCtipp.ch
3. A window will now open with the three options Replace Text, Add Text and Format. If you use the individual setting options, a current example is displayed at the bottom of the window so that you can see how the respective changes affect you.
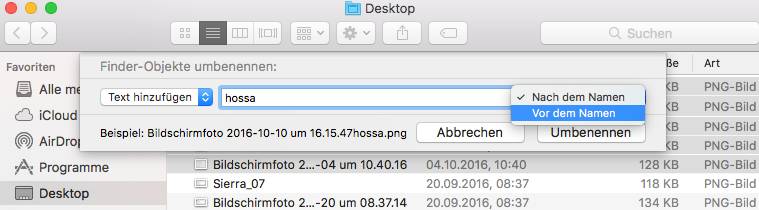 (c) PCtipp.ch
(c) PCtipp.ch
With a click on Rename all selected files will be renamed according to the selected format.
Finding and terminating clamping processes
On Mac OS it is possible to monitor processes and programs, respectively, to terminate them quickly. The option “Terminate programs immediately” is recommended especially if a program hangs. You can access this dialog window with the key combination Option + Cmd + Esc. You should always choose this procedure first when a program is stuck.
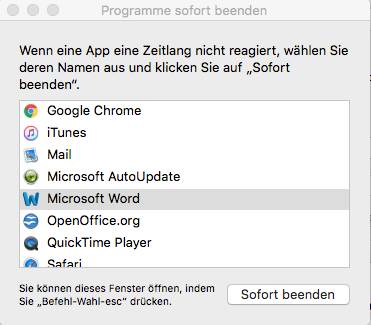 (c) PCtipp.ch
(c) PCtipp.ch
Where is the mouse pointer hiding?
It can happen before: the mouse pointer suddenly disappears from the screen, because perhaps a process is currently hanging in the background or because you are working on a huge screen. Then you may not know this trick yet: just move the mouse pointer back and forth for two seconds. As a result, the black arrow temporarily increases in size.
 (c) PCtipp.ch
(c) PCtipp.ch
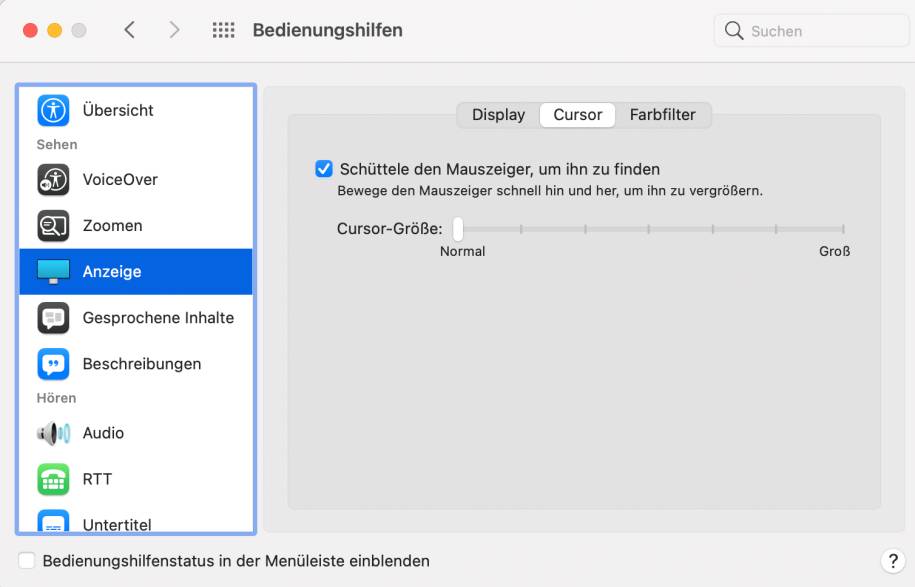
If you have already been disturbed by the temporary enlargement of the arrow, you can simply turn it off. The corresponding entry “Shake the mouse pointer to find it” can be found in the system settings under Accessibility/Cursor under Display.
 (c) PCtipp.ch
(c) PCtipp.ch
Delete files immediately
Sometimes you want to delete a suspicious file or an unimportant letter immediately, so that you do not have to move the file to the trash in the first place. This can be done in the Finder with the key combination Option + Command + Backspace.
Search better with Spotlight and Finder
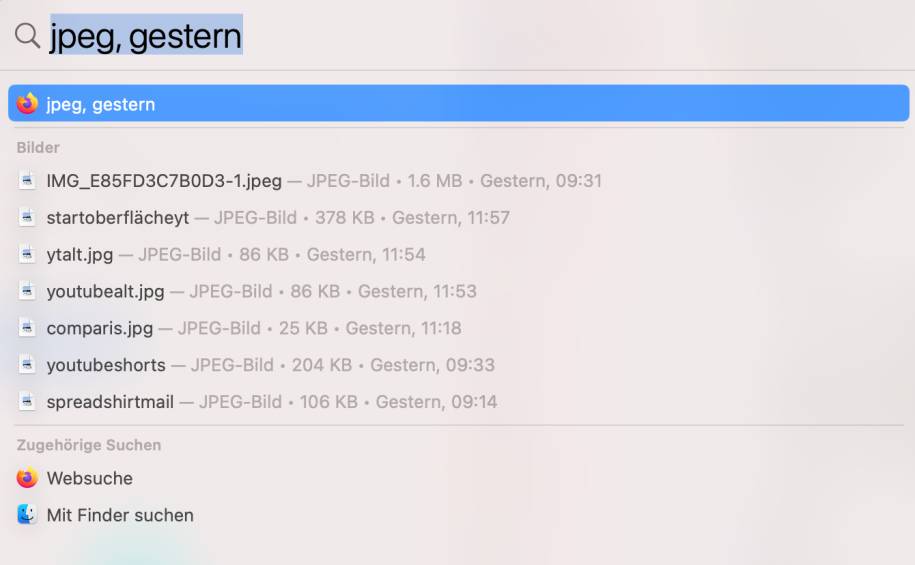
For old Mac bunnies, the Spotlight search function integrated in the system should be known for a long time. But what few people know: The Mac search function is also getting smarter and already differentiates between linguistic syntaxes. For example, as with Cortana on Windows 10, you can also type in a sentence like “Find me the Word document I was working on last week”. It can also be enough if you enter the file format and the tag, e.g. “jpeg, yesterday” You can reach Spotlight either via the Cmd+space bar or via the magnifying glass search symbol at the top of the menu.
 (c) PCtipp.ch
(c) PCtipp.ch
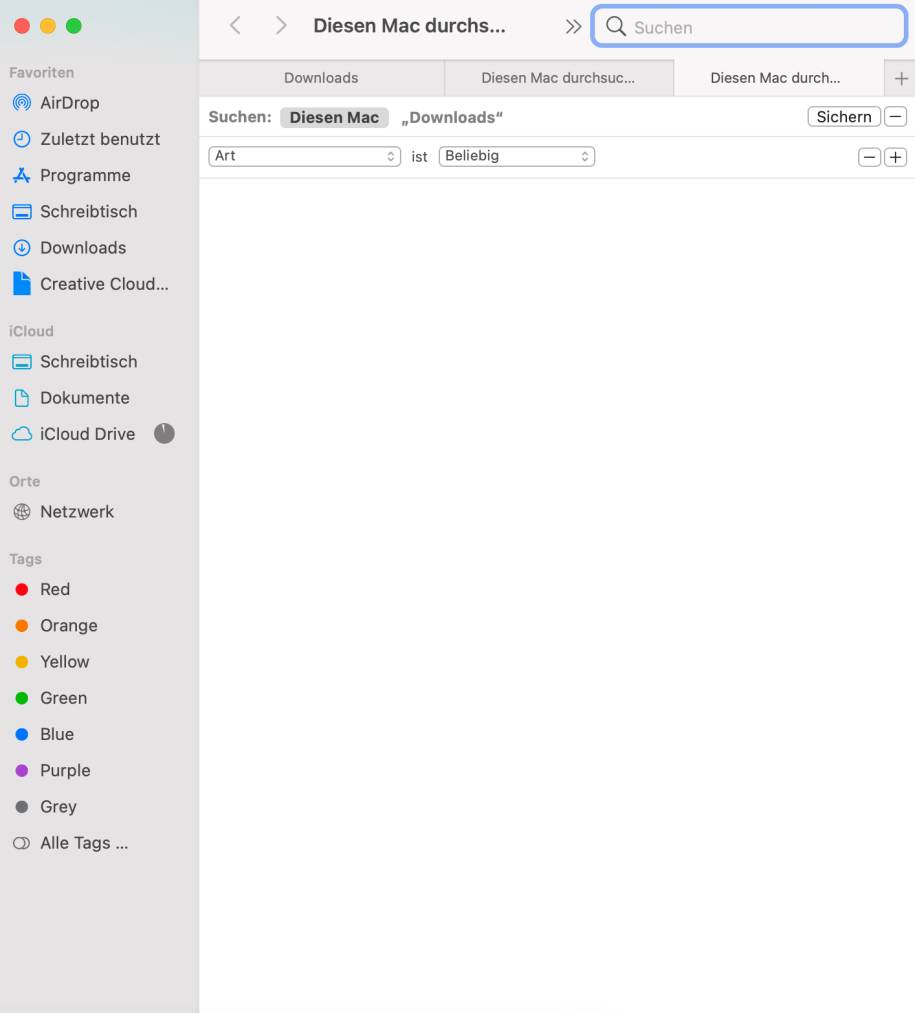
But what many do not know: Even the Finder offers an additional filter function, which opens with Cmd + F. Two drop-down menus offer additional filter criteria. For example, if you select “Art” on the left and “Image” on the right, you can use the “+”symbol to reveal further filters such as” Last modified date “or” Created date ” and use them in combination in the search.
 (c) PCtipp.ch
(c) PCtipp.ch
Work more efficiently with two windows
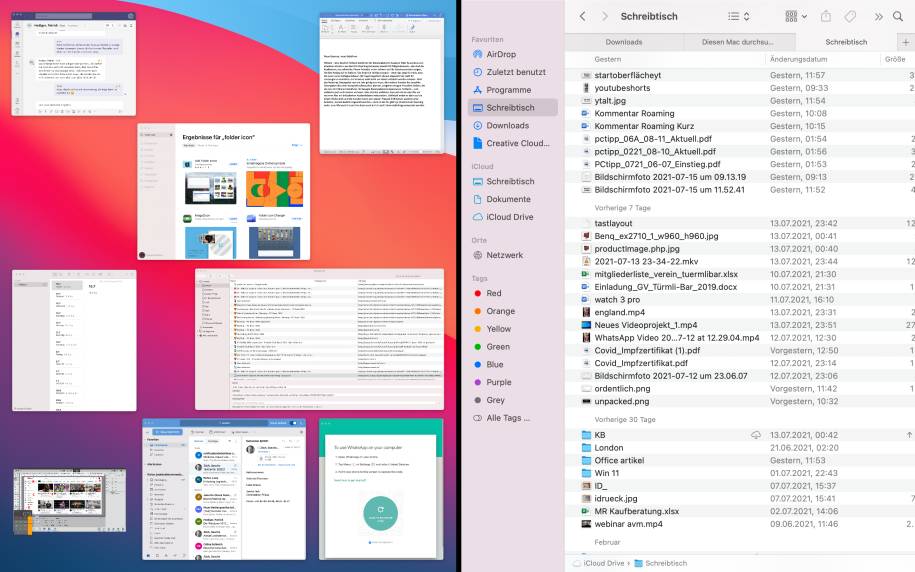
With the “Split View” function, you can quickly and easily separate the screen, for example, to navigate in the browser during browsing in the Finder in the window next door. The handling is a bit confusing at first, but it’s actually child’s play. This works mainly with Mac apps and not quite with all-but in between Split View is quite useful.
To use” Split View”, press and hold the green “circle icon” of the program window. When you hold down the button, a pop-up menu appears. You can now decide whether the current window comes into the left or right screen area, or switches to full screen mode. For example, if you select right, then all other open windows go into a miniature mode and you can choose which one should fill the left part of the screen.
 (c) PCtipp.ch
(c) PCtipp.ch
Smart Photo Search
Starting with macOS Sierra, more artificial intelligence came into play. Apple’s photo application is now able to recognize situations and objects in images. This simplifies one thing above all: the quick search! The first time you start the application, the application takes a while, depending on how many images you already hoard on your Mac. You can now simply search for a keyword such as “Computer” using the search field of the Photos app (alternatively also using Cmd+F).
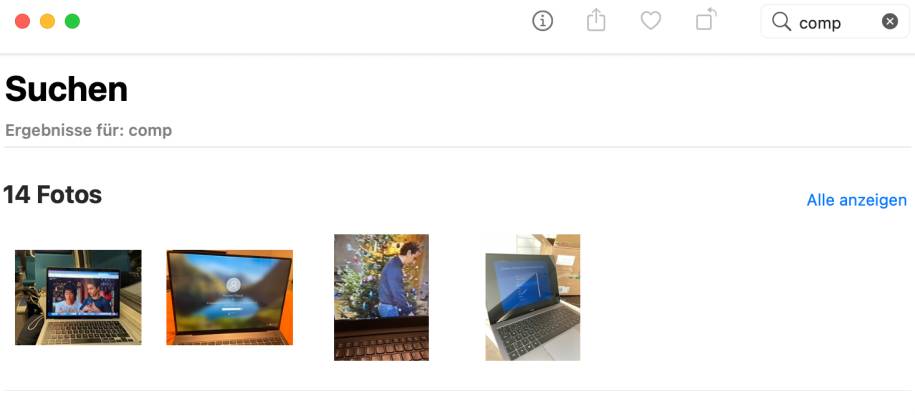 (c) PCtipp.ch
(c) PCtipp.ch













