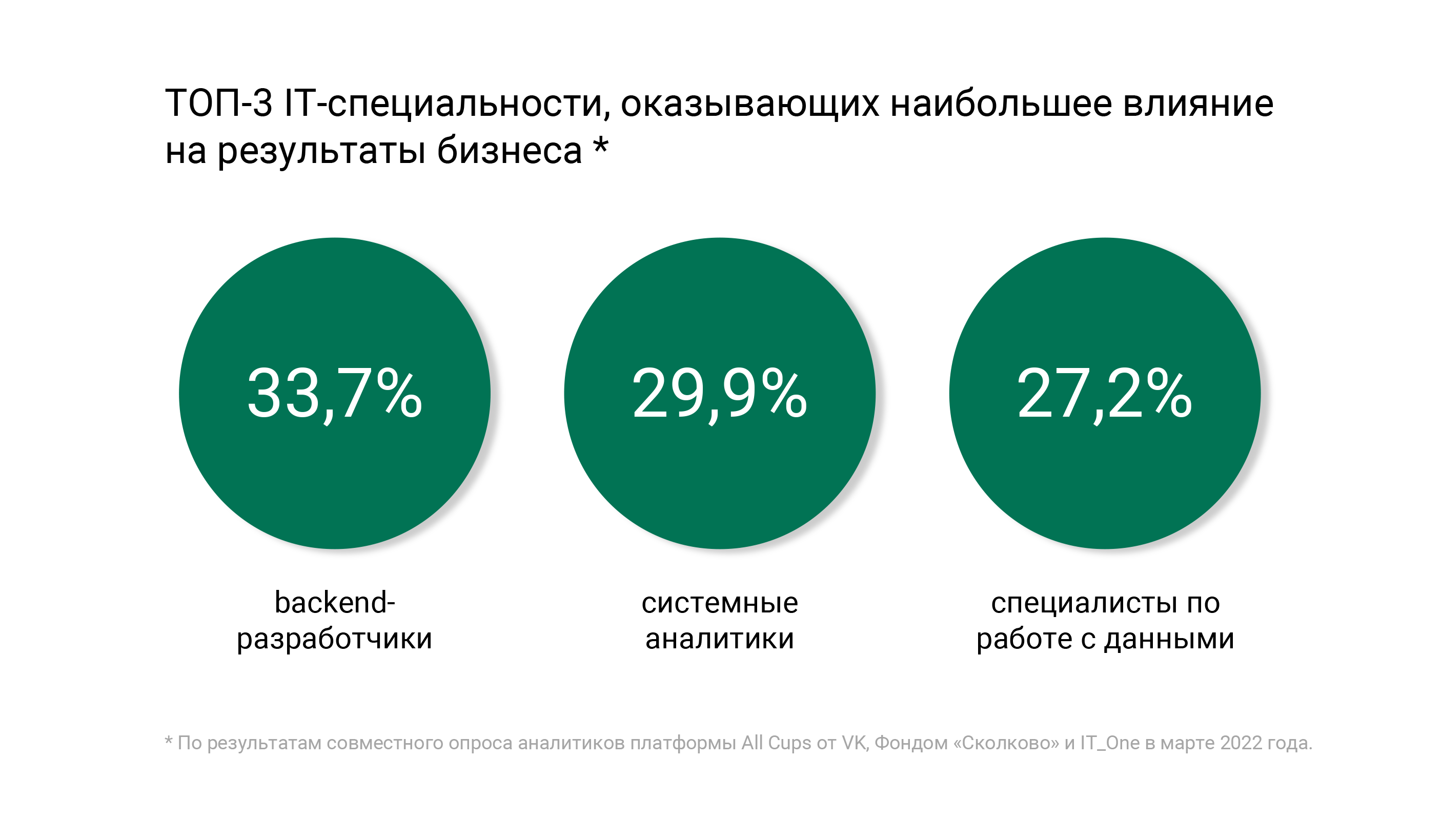
The demand for IT specialists is growing many times, so the crisis is not the time to stop in career development. At the same time, the rules of the game have changed.
Don’t panic
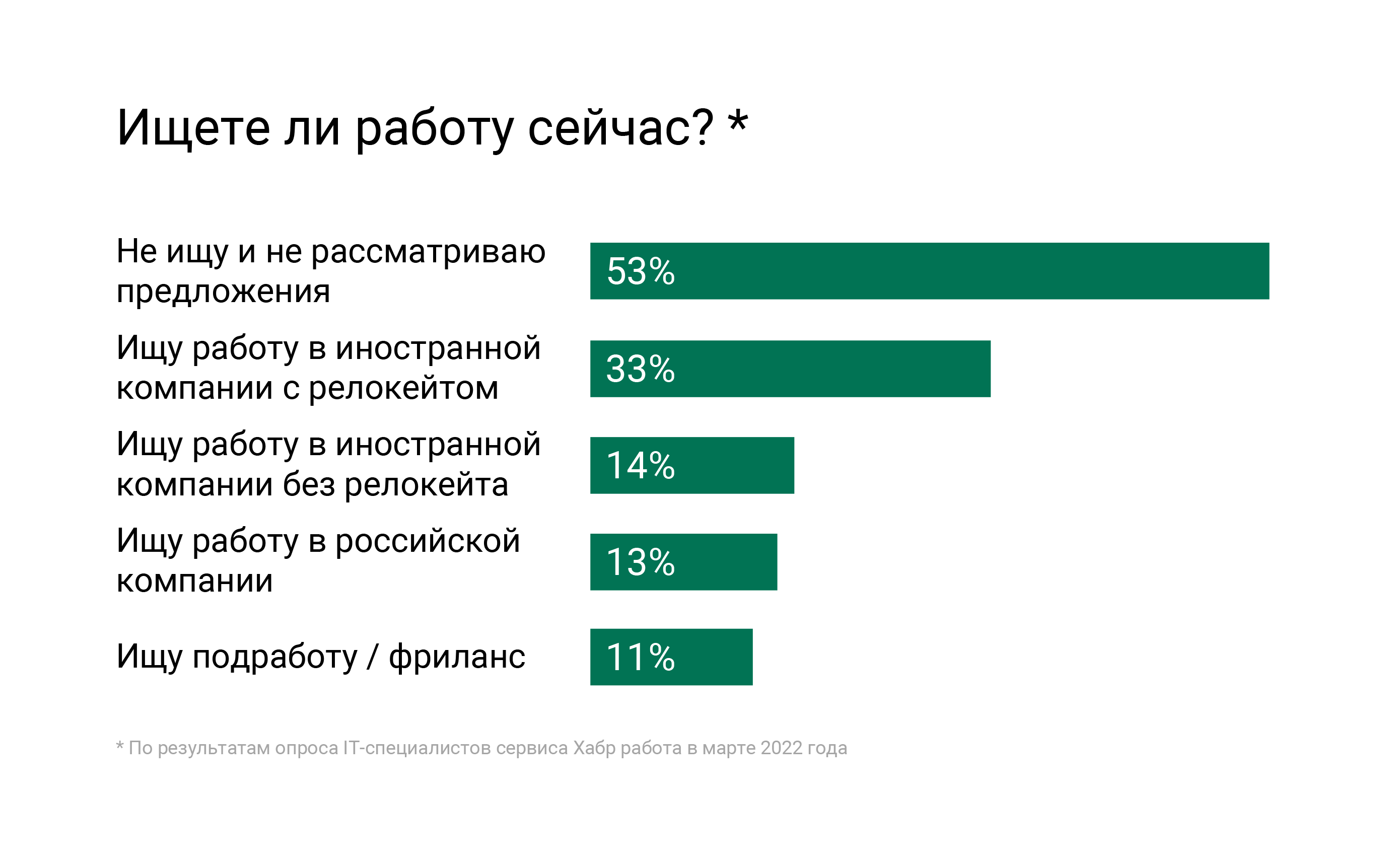
We have all fallen into a new reality and we cannot count on the previous relatively calm course of life. Everyone reacts to the crisis in their own way: someone freezes, someone starts chaotic activity – an alarming news background contributes to this. According to a study by Habr Career, 47% of IT specialists are looking for work, and 33% are considering relocation.
The main advice now is not to panic and not to let emotions cloud your mind. Any decision, be it relocation or change of specialization, should be balanced, it is important to take into account all the risks and assess the available resources.
If we take, for example, relocation, there is a risk of reducing the cost of IT specialists from the Russian Federation due to excessive demand from candidates. You need to be prepared for this and think through the sequence of steps to level the risks in advance.
Consciously approach the choice of country before relocation
In my opinion, all markets are open for Russian IT specialists now, as before. The difficulties are rather related to the restrictions imposed on banking operations for Russian residents, but this issue can be resolved. It is important when choosing a relocation and, in general, when choosing a country of residence, to consciously work out both everyday issues (housing, food, availability of stable Internet) and to get an offer or employer’s consent to move in advance.
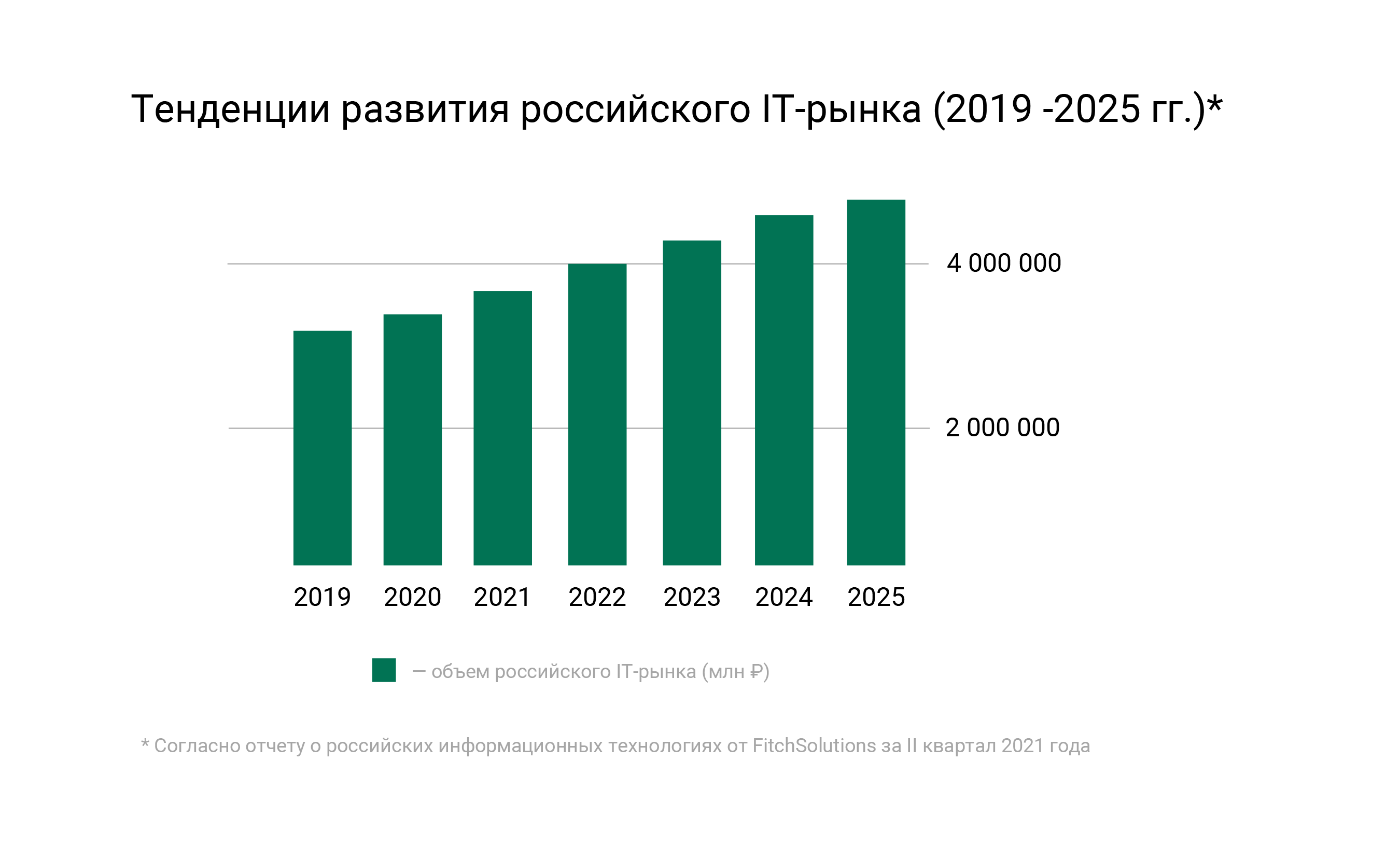
IT specialists are desperately needed by many companies in Russia: at the beginning of 2022, the shortage of developers was about 1 million people. At the same time, the business is aware of the role of developers in providing leadership in the market, and is ready to offer specialists a higher level of income.
It is difficult to say where the salary is higher: global companies usually have a higher compensation level, but it includes not only a fixed part, but also bonuses, benefits for employees, for example, a relocation package. Therefore, you need to look at the income in aggregate, sometimes the salary is average, but the benefits cover many household needs, for example, payment for accommodation, meals, children’s education, and it turns out more profitable. Startups often offer options, which can also be interesting in the long run.
If we talk about which markets IT specialists should pay attention to, these are Kazakhstan, Dubai, Uzbekistan, Estonia, Armenia, Georgia. It is worth going to Cyprus if you are interested in the development of cryptocurrency projects.
On In the East, China ranks first in the number of startups, but knowledge of the language is required to work in the market. They are mainly looking for IT specialists for the development of various infrastructures. Frontend and backend are in demand, but they don’t offer a lot of money. At the same time, the Chinese market is quite self-sufficient: there are many provinces inside the country, the need for developers is first closed inside the country, or with the involvement of specialists from neighboring countries, besides ― Vietnam, Thailand and so on. There is a very interesting market in South Korea, where the financial sector is very developed, startups are also actively growing there.
Think over a career track
IT specialists will always be in demand, but the market is changing, and with it career trajectories. Companies are willing to pay more, but in the future they are very attentive to the potential value of employees for business. In the next couple of years, the market will face serious challenges, and in order to get to the point where you want to be, it is important to think over a career track right now: to communicate with a manager, HR specialist or career consultant and form a strategy to achieve the goal.
Develop expertise
I recommend devoting an independent choice to those competencies and technologies that already have expertise. Pumping skills in new areas in a crisis can be too risky an investment of effort. Conditionally, it would be more reasonable for a JAVA middle developer to focus on the growth of the grade to a JAVA senior developer, as opposed to immersion in mobile development with zero experience. In addition, it is worth paying attention to pumping skills from related areas: in addition to programming, it will be cool to add the ability to test or think through the architecture of the product.
If we talk about popular programming languages, then everything is standard here: in the top golang, JS, React/Angular. In the USA, the trend for no-code development is increasing, but it has not reached us yet.
Useful sources
Read about the Go programming language (golang):
Learning the React / Angular framework:
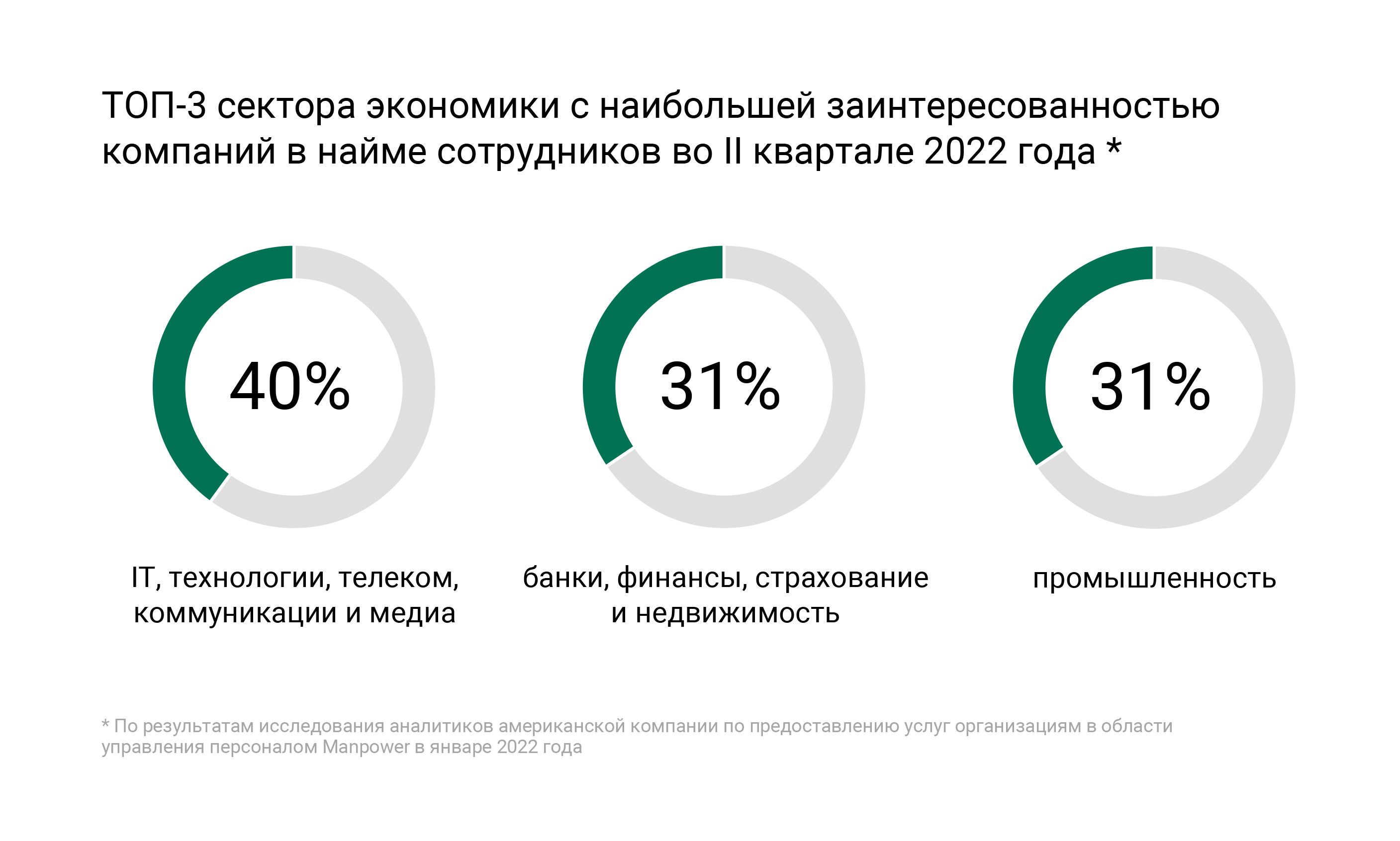
Choose sustainable companies
Of course, the stability of the current business model of the employer company in the new conditions and the growth rates of the market segment that it occupies are important. In addition, it is important to assess the company’s willingness to invest in employee training and development. Firstly, it means that the company feels good in the current conditions, and, secondly, the ability to pump skills implies a competitive stable salary in the future. It is also worth looking at startups and small companies: they adapt faster due to the flexibility of processes.
Pay attention to the industries focused on import substitution
In my opinion, in the near future, specialists in the areas related to import substitution will be most in demand: the development and implementation of 1C modules, cybersecurity, hardware infrastructure management. In addition, oil and gas, engineering, graphic products, as well as CRM/ERP systems are among the problematic ones for import substitution according to the Ministry of Finance. In addition, gamedev specialists and mobile application developers are needed, since in these areas I assume the maximum outflow of specialists outside the Russian Federation.